5-Step Security Compliance for Small and Medim Buisnesses
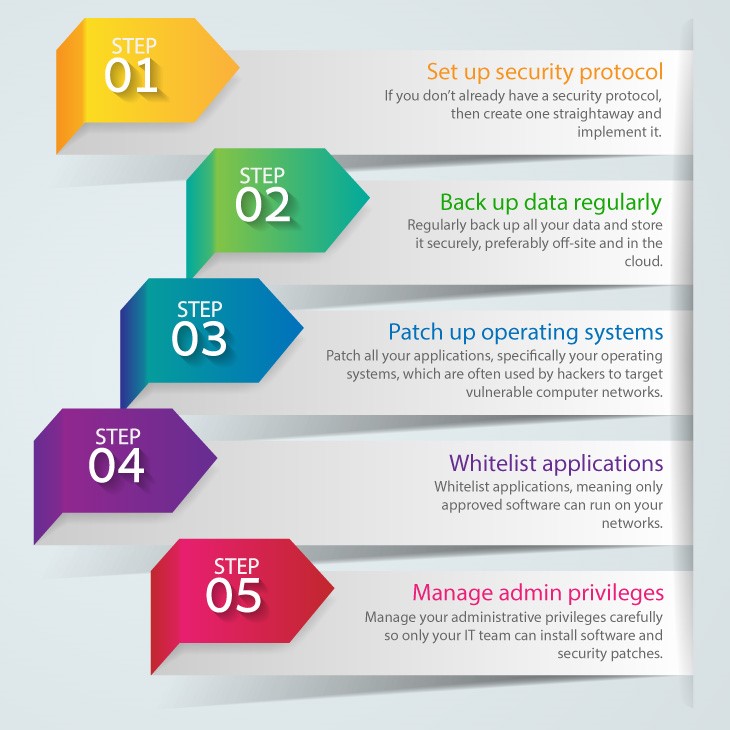
5 steps to make sure your SMBs are security compliant

5 steps to make sure your SMBs are security compliant


Time to go on the offense with IT security

. What challenges do businesses face and how can executives prevent sleepless nights over the network security issues?

For most businesses, the question isn’t if they will be hit by ransomware, but when.

Antivirus doesn’t cut it anymore. You need a multi-layered, sophisticated approach to endpoint security. Here’s what you need to know:

Hardware and software running beyond their end-of-life dates are serious hazards. Find out which assets you should update, upgrade, or replace.

Every business can benefit from a well-considered BYOD policy. But what security factors do you need to consider when putting yours together?

Last year was the worst on record for information security threats, and the majority of those were due to inside sources, many studies agree.

Are your network ‘endpoints’ – the PCs, phones, tablets (and more) you use to access information – as secure as they should be?
Since 2005, we have enabled businesses along the Gulf South to move forward with innovative, tailored IT solutions and services, delivering on our brand promise of “Right Solution, Right Response, Right Now!”
| Monday | 8 AM – 5 PM |
| Tuesday | 8 AM – 5 PM |
| Wednesday | 8 AM – 5 PM |
| Thursday | 8 AM – 5 PM |
| Friday | 8 AM – 5 PM |
| Saturday | Closed |
| Sunday | Closed |