Ransomware Is No Joke
You may be aware that ransomware attacks have doubled this year.
If you’ve been the victim of such an attack, or you want to take preemptive measures to prevent one, you’ve come to the right place. At Gulf South Technology Solutions, we’ve rescued many businesses from ransomware — in fact, the businesses we protect haven’t experienced a ransomware attack in over three years.
To understand options for resolving ransomware issues, first let’s discuss how individuals are targeted with ransomware, and what factors make them vulnerable.
How Does Ransomware Work?
Typically, ransomware is delivered via a phishing email. You’ll receive what appears to be an ordinary email, but it contains a deadly link that, when clicked, ultimately grants a hacker complete access to your network. Some delivery methods can be even stealthier, as they require no clicking error on your part but simply make their way in from a variety of unknown security gaps.
Once it gets in, the ransomware encrypts the files on your network, making them inaccessible. You’re effectively barred from using your computer, and you may receive a “ransom note” like this one:
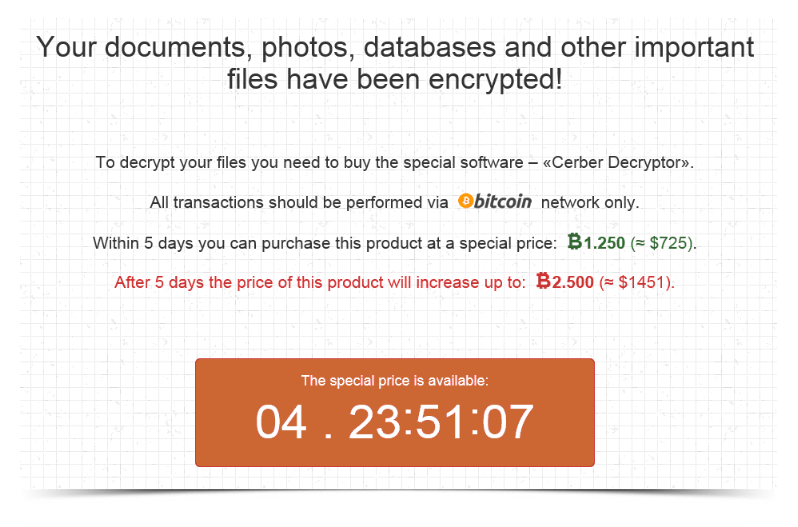
This is an ACTUAL screenshot was sent to us by an infected business.
The ransom figures have changed dramatically; the price of one bitcoin today is about $8,200. But the principle remains the same:
You have 5 days to pay before the ransom doubles.
All your files have been encrypted, and you cannot retrieve them without paying the ransom.
How Do You Get Rid of Ransomware?
You generally have two options.
You can purchase the demanded bitcoin (which is not so easily accessed) and send it to the anonymous address requested. Below is the follow-up message to the ransom demand, with the address information:

But note this: Paying the ransom doesn’t guarantee you’ll get your data back. Frequently the hacker doesn’t even have the decryption key, so paying the ransom is a gamble.
Your alternative option is to restore your files from your last successful backup, although it’s possible the backup has also been encrypted. And while some computer users are performing backups more consistently, many still don’t. A good backup strategy backs up your files automatically. But, more often than not, companies skimp on their backup.
75% of SMBs don’t have a continuity policy
If you go with the most hands-off, cheap option and don’t know the last time your network was successfully backed up, you’re the most vulnerable, as those are the easiest networks to encrypt.
Without a viable backup, you’ll be forced to pay the ransom to prevent the permanent loss of your files.
Preventing Ransomware?
Your best strategy is to have security protocols in place before ransomware hits you. We recommend the following:
- Keep your operating system up to dateWhen new updates become available, don’t hesitate to install them. Updates likely contain security patches to upgrade the protections on your devices, enhancing your ability to ward off ransomware attacks.
- Set privilege standards, and don’t fall for phishingNever install software for or give administrative privileges to anyone who doesn’t require them. Train your staff to recognize phishing emails to prevent user-triggered infection, and give them the tools they need to combat them.
- Install security softwareAntivirus, anti-malware, and other security software erect a barrier against ransomware by detecting malware as it arrives and preventing your computer applications from executing malicious files.
- Back up your files!This is the single most important prevention policy. Consistently backing up your files on a separate server and in the cloud can severely reduce the impact of a ransomware attack. If your files are up to date in a separate backup drive, ransomware can be averted by simply restoring your files. But frankly, many procrastinate, putting it off until it’s too late.
This is how we protect our customers from ransomware — by regularly updating their systems, automating a backup profile schedule to a secure cloud server, and running regular scans to intercept threats that may be lurking in their networks.
What Happens After Ransomware Is Removed?
Even if you pay the ransom, you must assume that all sensitive data has been compromised. Usernames, passwords, payment information, email addresses, sensitive client information — the very things requiring protection most — may have been acquired by the hacker.
Once the bug is eradicated you need to reset all security protocols. Change passwords, re-install security programs, check permissions, clear your cache, and alert your bank to change online billing information.
And as unpleasant as the task is, you must inform your contacts of what has transpired (especially if you’re in finance or healthcare — some of ransomware’s biggesttargets), cautioning them to be alert and not to open suspicious emails or files. Depending on your industry, you may have a legal obligation to disclose this to your customers, as well.
If you’re ready to remove ransomware or add a protective program to prevent it in the first place, let’s chat.



